2.1 KiB
layout, title, date, comments, tags
| layout | title | date | comments | tags |
|---|---|---|---|---|
| post | On captive portals | 2019-04-05 | true | firefox, privacy |
Following is a rant, feel free to just skip it. You've been warned.
Captive portals are bad! For the unitiated, they are the annoying websites you have to click through on public hotspots, Demanding an arm, leg or just your email address.
Most of them work by hijacking HTTP pages1 , for any http pages visted before "authenticated", one would get a temporary redirect to the captive portal url. But most of the popular websites deploy HSTS, which would instruct the clients to never even hit HTTP version of their server. Try asking firefox to goto http://google.com - it would force rewrite it to https before sending even a peep out.2
So in an alternate life you'd be staring at your browser waiting for
google.com that never loads. Browsers and OSes workaround this problem
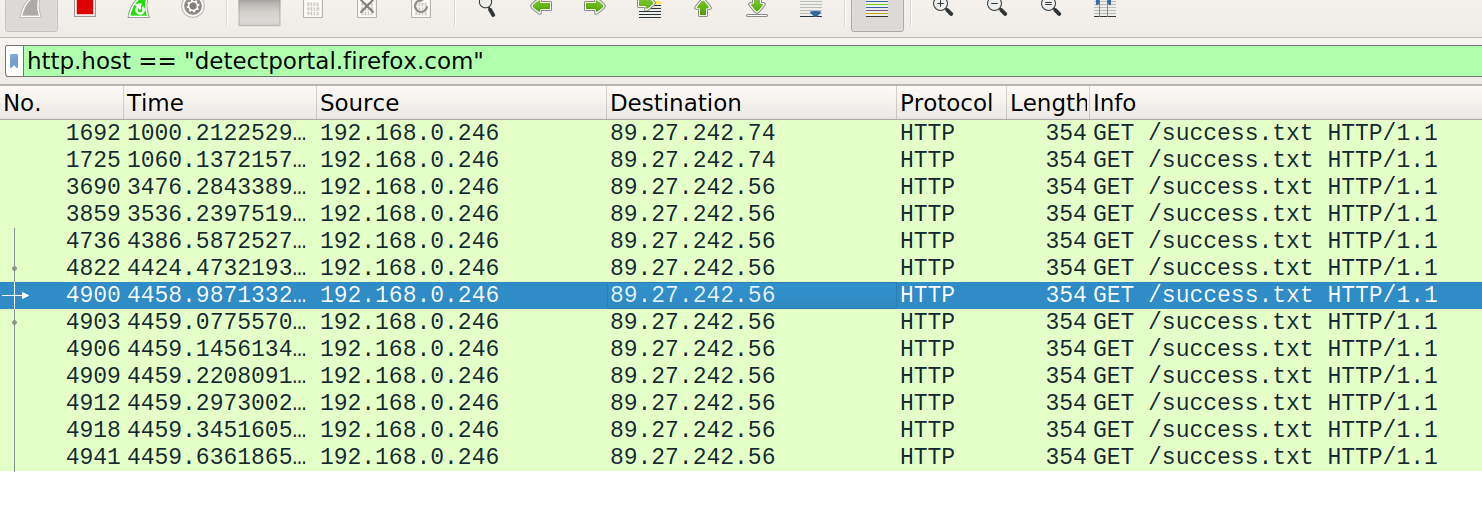
by detecting captive portals - Firefox does this by trying to fetch
http://detectportal.firefox.com/sucess.txt, and if it doesn't come
back assume the browser to be behind a portal.
Firefox keeps making this requests periodically, and its kinda annoying to me because its the networking version of "lit like a christmas tree".
One could turn off firefox's behavior by toggling
network.captive-portal-service.enabled in about:config. But then
you are responsible for manually going to an HTTP-only url after
connected to a public hotspot. The same firefox url should be
fine.3
I understand that there are "legal" requirements to setup captive portals (or other reasons?, enlighten me). But after you "authenticate" most systems grant you access by your MAC and/or IP. Both of which someone motivated can easily sniff and spoof.
So yeah, I think captive portals are BAD.